Cybercrime Alert: ErrTraffic Cybercrime Tool Automates ClickFix Attacks, Trick Users Into Running Malware
Once compromised, victim devices can have login credentials stolen, allowing attackers to hijack additional websites and expand the campaign further, writes Santhosh Kumar
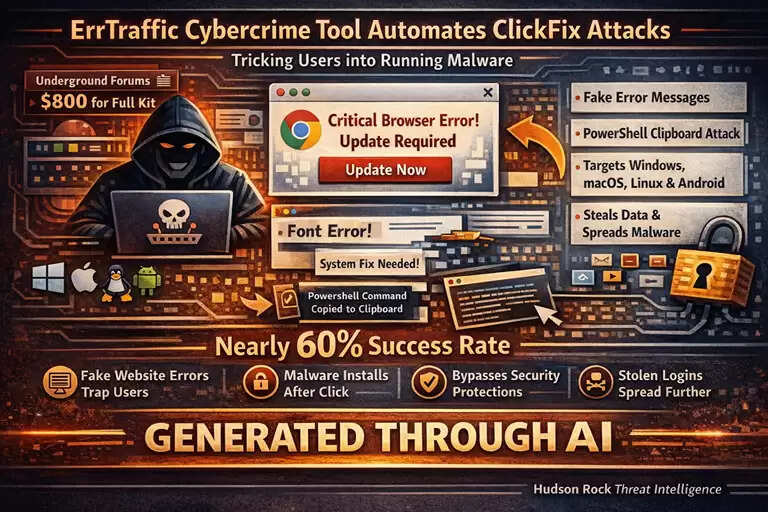
Udaipur, Jan 16, 2026: A newly discovered cybercrime tool called ErrTraffic is circulating on underground forums, significantly lowering the barrier for attackers to trick users into executing malicious software on their own devices.
ErrTraffic automates a growing attack technique known as ClickFix, which relies on fake error messages to convince users to manually run harmful commands. Instead of silently downloading malware in the background, ClickFix attacks exploit user trust by simulating website errors that appear to require immediate fixes.
How ClickFix Attacks Work
Rather than hiding malicious downloads, ClickFix attacks display convincing website glitches—such as broken text, distorted fonts, or corrupted layouts—making the page look faulty. Victims are then prompted to “fix” the issue by updating their browser or installing a missing system component, which leads them to execute attacker-controlled commands.
Why ErrTraffic Is Dangerous
What makes ErrTraffic particularly alarming is its professional design, automation, and affordability. Even low-skilled cybercriminals can launch sophisticated attacks across multiple platforms, including Windows, macOS, Linux, and Android.
The tool was first identified in early December 2025 on Russian-language cybercrime forums, where it was advertised by a threat actor using the alias LenAI. For approximately $800, buyers receive the full ErrTraffic package, including a centralized control panel and scripts capable of deploying realistic fake errors on compromised websites.
Technical Operation
According to analysts from the Hudson Rock Threat Intelligence Team, ErrTraffic works through a simple JavaScript injection. Once attackers gain access to a website, they only need to insert a single line of code that connects the site to their command-and-control panel.
The script automatically detects a visitor’s operating system, browser, and language, then displays a tailored fake error message. A common lure involves a fraudulent “Chrome Update” or missing font notification.
When users click the fix button, a PowerShell command is copied to their clipboard, with instructions to paste and run it manually. This approach effectively bypasses traditional security defenses, as browsers treat clipboard actions as normal behavior and endpoint security tools see PowerShell execution as user-initiated.
High Success Rates and Payloads
Analysis of active ErrTraffic campaigns shows alarming success. Dashboard data from real-world attacks reveals conversion rates close to 60%, meaning a majority of users exposed to the fake errors end up executing malicious code.
Attackers typically deploy infostealers such as Lumma or Vidar on Windows systems, while Android victims are targeted with banking trojans. The control panel also includes geographic filtering, deliberately blocking infections in Russia and nearby countries to reduce the risk of local law enforcement attention.
A Self-Propagating Threat
Once compromised, victim devices can have login credentials stolen, allowing attackers to hijack additional websites and expand the campaign further. This creates a self-sustaining infection loop, where stolen access fuels the next wave of attacks.
#ErrTraffic #ClickFixAttack #CyberCrime #CyberSecurityNews #MalwareAlert #OnlineScam #BrowserUpdateScam #PowerShellAttack #Udaipur #Rajasthan #UdaipurNews #RajasthanNews #TechNewsIndia #DigitalSafety
FAQ SECTION:
What is ErrTraffic?
ErrTraffic is a cybercrime tool that automates ClickFix attacks by displaying fake website error messages to trick users into running malicious commands.
What is a ClickFix attack?
ClickFix attacks rely on social engineering, convincing users to manually “fix” fake browser or system errors by executing attacker-controlled commands.
Why is ErrTraffic dangerous?
ErrTraffic lowers the skill required for cybercrime, offers automation, and bypasses security tools by making malware execution appear user-initiated.
Which devices are affected by ErrTraffic attacks?
ErrTraffic campaigns target Windows, macOS, Linux, and Android users.
How can users protect themselves?
Users should avoid running commands from pop-ups, ignore fake update warnings, and ensure browsers and operating systems are updated only through official sources.
To join us on Facebook Click Here and Subscribe to UdaipurTimes Broadcast channels on GoogleNews | Telegram | Signal